SNARE CENTRAL
The Log Management Platform of Choice for the Global Fortune 2000 and Top MSSPs
Supporting your security and compliance needs
Our enterprise-level yet flexible log management solution, Snare Central helps organizations crush their security goals.
- Over 600 out-of-the-box and customizable report
- Collect any logs from anywhere
- Filter out event and log noise
- Customize what data goes where
- Ingest syslog feeds from any device
- Over 100 log adapters to parse common syslog data
- SNMP trap alerts from network devices
- Batch bulk uploads of archived data
SNARE CENTRAL
Improve Threat Hunting Speed & Investigation Capabilities
Snare Central introduces several updates designed and developed to dramatically improve threat hunting speed and investigation capabilities, maximizing the effectiveness of the SOC.
The latest version of Snare Central features:
- Snare Management Center (SMC) – A centralized management view of multiple Snare Central systems, eliminating the need to visit each system on-site.
- Enhanced automated alerting to improve threat hunting speed
- New log types to expand coverage and enhance investigation capabilities
- Cloud-based log management and reports to support cloud or hybrid environments
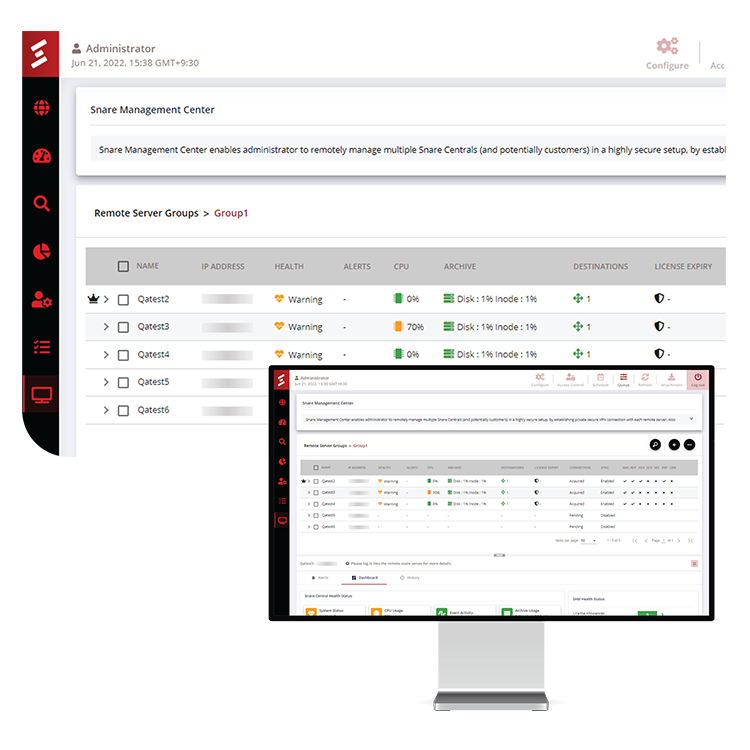
Snare Management Center for Enterprise & MSSPs
For large enterprise organizations or MSSPs, the Snare Management Center (SMC) will provide users with the ability for centralized management of policies for AMC, Reflector, Reports, Users, Schedules, Health Checker for Snare Centrals remotely via a new centralized management view of multiple Snare Central systems.
Cyber Network Map to Improve Visibility
Snare Central v8.5 introduces a real-time cyber network map, designed and developed to dramatically to help security teams quickly geo-locate potential threat actors or anomalous activities.
Cloud Log Collection and Reporting for Microsoft 365 & Azure
Expanded cloud-based log management capabilities enable users to collect, manage, and report on cloud-based activity. This includes monitoring administrative activity, capturing failed logon logs, or alerting to changes made to mail boxes or overwriting information.
Enhanced Automated Alerts to Improve Threat Hunting Speed
Speed is everything when it comes to cybersecurity. Enhanced automated alerting will notify your SOC or security analysts immediately to potential threats or anomalous activities in your system, enabling your team to respond to a threat and gather critical information in a matter of minutes.
Expanded Reporting Capabilities for Cloud and Hybrid Environments
Snare’s expanded report library now includes over 50 cloud log reports, Cisco fire-powered threat defense reports, and Kernel-based activity reporting.
New Log Formats for Expanded Coverage
New log formats mean expanded coverage for more granular audit and forensics capability. This update will add enhanced support for Microsoft Sentinel, CEF, SQL, and Linux.
Forrester 2022 Security Analytics Landscape Review
Forrester’s Overview Of 30 Providers: Including Prophecy International & Snare
Enterprise Level Management
SNARE MANAGEMENT CENTER
The Snare Management Center (SMC) will provide users with the ability for centralized management of core settings via a new centralized management view of multiple Snare Central systems. This central management capability is designed for enterprise customers with multiple Snare Centrals and/or MSSPs that manage multiple customers across different locations or geographies.
- Save time on visiting each system for status updates or managing configuration
- Ensure consistent application of security policies, alerting, and reporting across your organization
- Monitor the health status of all Snare systems via one single view
- Immediately alert your SOC or IT stakeholders to specific systems showing problems or anomalous activity so they can be investigated in minutes
- Save time and resources by centrally configuring core settings: AMC Policies, Reports, Health Check, Objective Schedules, Reflector Configuration, User Access
- Secure remote access over SSH or OpenVPN
Geo-Locate Threats in a Fraction of the Time
CYBER NETWORK MAP
Based on live network-related events, Snare’s real-time Cyber Network Map will help security teams quickly identify potential threats and locate the source in a fraction of the time. The interactive 3-D globe and world map enables users to visualize, explore, and geo-locate the source of potential threats or activities that require further investigation.
The highly visual 3-D cyber network map means faster time-to-detection of unusual or unauthorized network activity. This dramatically improves the speed at which a SOC or security analyst can:
- Visualize network activity
- Identify the country of origin, source and destination IP addresses, ports, and more
- Detect and identify unusual threat traffic patterns for internet-facing systems and network devices
- Detect the exfiltration of data
Extended Cloud Capabilities
Log Reports for Microsoft 365 & Azure
As many organizations migrate to a cloud-based architecture, it is critical to monitor cloud logs. With the addition of over 40 new cloud reports for Office 365 and Azure, users can effectively monitor and report on activity from Microsoft environments.
Expanded cloud-based log management capabilities enable users to collect, manage, and report on cloud-based activity.
- Monitoring administrative activity
- Capturing failed logon logs, or
- Alerting to changes made to mail boxes or overwriting information
New Log Formats
Extended Event Coverage for SQL, CEF, and Cisco Threat Defense
Snare’s log collection and reporting capabilities have been extended to support Cisco Firepower Threat Defense and Common Event Format (CEF) log types.
The addition of these new supported log formats mean:
- More granular audit and forensics capabilities
- Extended event coverage
- Better support & reports for Microsoft Sentinel & other SIEMs that process CEF formats
- Better support and reports for Cisco Firepower Threat Defense logs
Improve Threat Hunting Speed
Real Time Alerting
Enhanced automated alerting will notify your SOC immediately to potential threats or anomalous activities in your system, enabling your team to respond to a threat and gather critical information in a matter of minutes.
In the event of a breach or an attack, your organization may have as few as 24-hours to answer these critical questions. Snare will enable your SOC to answer these questions in a matter of minutes vs months:
- Who got in
- How did they get in, and
- What did they take?
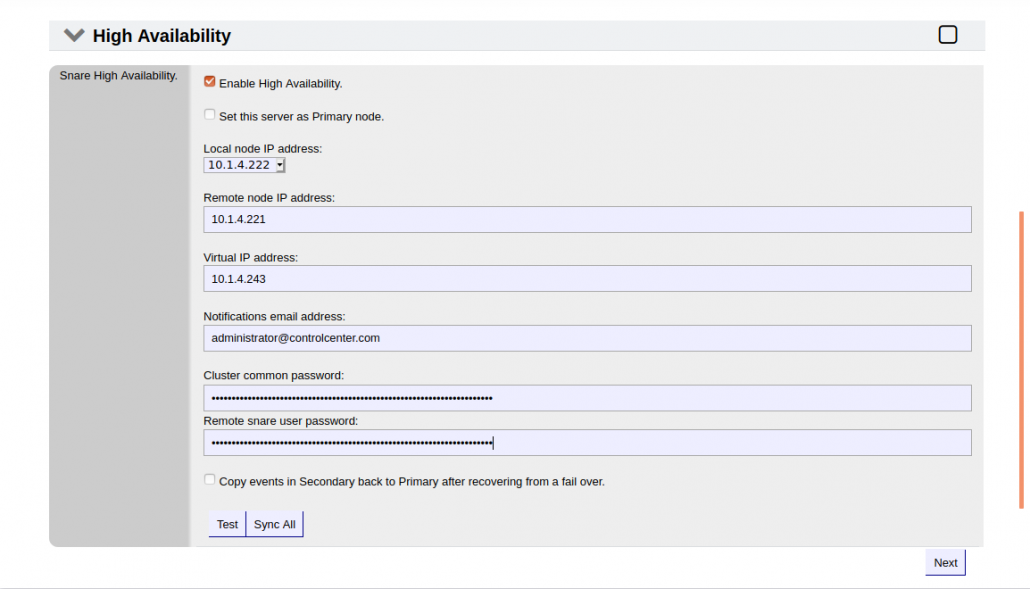
High Availability
MINIMIZE THE CHANCE OF LOSING LOG DATA
High Availability helps to ensure there is minimal chance of lost log data, which is critical for forensic analysis in the event of a cyber attack or breach. High Availability also helps meetregulatory compliance requirements such as GDPR, ISO27001, and PCI DSS.
With High Availability, security teams can:
- Reduce the risk of losing log data, in particular UDP-based systems where data can be lost more easily
- Have more resiliency in log collection
- Reduce the need for caching when systems can failover
- Make it easier to reflect to two or more “master” collection Centrals or SIEM systems
- Separate hardware provides better redundancy
- Distribute the load over multiple clusters
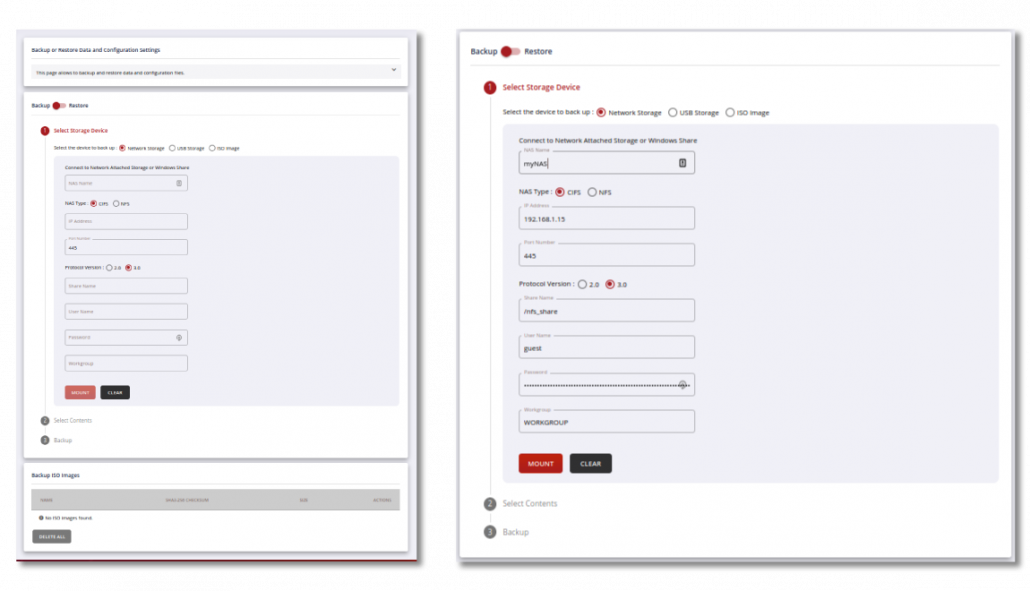
Backup & Restore
BACKUP & RESTORE LOG DATA FOR FORENSIC ANALYSIS
Snare Central’s simple Backup & Restore feature helps to save on downtime and system rebuilds. With Snare’s Backup & Restore capabilities and the ability to workflow the process with scheduled backups, security teams can quickly, easily, and automatically recover log data for forensic analysis or use disk manager to view log data from backup locations.
Simply put, Snare Central makes sure your company’s valuable log data is there when you need it:
- Easily restore and select components
- If a user makes a mistake or breaks their Snare Central configuration, they can recover the components from backup
- Small workflow of steps required
- Flexible backup options and granular recovery of Snare Central components or system logs
- Flexible options for backup destinations – NAS, USB, ISO, DVD for long term storage or immutable media
Snare Reflector
COLLECT MORE LOGS FROM MORE SYSTEMS
Snare Central’s Reflector makes it easier for security teams to collect logs from more systems. The Snare Reflector provides enriched data to third party SIEM systems, improving performance and scalability.
With the new Snare Reflector, security teams can enhance their log collection and log management capabilities with:
- New log formats such as JSON
- Improved disk caching that requires less admin to manage
- Enhanced ability to collect logs at higher eps rates on the same hardware
- Additional log formats for compatibility with other third party SIEM systems
Snare Central Capabilities
– Experience the Full Suite –
AUTOMATED ALERTING
Snare automated alerts notify your SOC or security analyst(s) immediately if there is a potential threat or anomalous activity in your system.
THREAT INVESTIGATION CAPABILITIES
Snare includes FIM/FAM/RIM/RAM/USB and Database Activity Monitoring to answer critical questions in a matter of minutes: who got in, how they got in, and what they took.
UNLIMITED, PRISTINE DATA STORAGE
Improve compliance and save money by compressing and storing an unlimited number of log data for the required timeframes in a pristine environment – logs may be required to be stored and untouched for 7+ years.
HIGH AVAILABILITY
High Availability helps to ensure there is minimal chance of lost log data, which is critical for forensic analysis in the event of a cyber attack or breach. High Availability also helps meet compliance regulatory requirements such as GDPR, ISO27001, and PCI DSS.
BACKUP & RESTORE
Helps to save on downtime and system rebuilds with simple Backup & Restore. Recover log data for forensic analysis or use the disk manager to view log data from backup locations.
600+ REPORTS | XDR & SYSMON
Over 600 reports cover new log types and threat hunting enhancements using Sysmon and additional log sources.
COLOR CODING BY CRITICALITY
Report criticality is now visible on report icons. Users can set up reports based on criticality levels and what the they deem to be Low Priority (green) to High Priority (red). You can also filter your reports by criticality so you’re always focused on what’s most pressing.
DEDICATED TLS SYSLOG PORT
Snare Central includes a new dedicated TLS listener port for syslog collection.
NETWORK STORAGE FOR BACKUPS
Redundancy is critical in cybersecurity compliance and Snare Central now supports Network Storage (CIFS or NFS) to back up your collected log data.
ENHANCED FILE INTEGRITY CHECK ADMINISTRATION
This tool allows the user to schedule, monitor, and administrate system files integrity checks and report on any changes on such files.
SNARE ENTERPRISE AGENTS
The industry’s best for Windows, Linux, Unix, macOS, Epilog, etc. – including FIM, RIM, FAM, RAM, and USB solutions. Windows Agents Veracode Verified. No Java or .NET required
24x7x365 SUPPORTS
We have customers all over the globe and on every continent, so we are here to support you whenever you need it.
Ask Us About Snare Central
Get in touch with your regional Snare office about upgrading or deploying Snare.