Snare Product Update
Highlighted by enhancements to data granularity, File and Registry Activity Monitoring (FAM/RAM), and extended SQL coverage, the latest version of Snare Enterprise Agents will help provide security teams worldwide with immediate access to the level of event log data that is essential for meeting mandated cyber incident reporting requirements as well as the type of detailed data that security teams require to improve threat hunting capabilities and speed-to-detection of anomalous activities:
- Who got in?
- How did they get in?
- What did they take?
The updates to the Snare Enterprise Agents will help ensure that security teams have immediate and reliable access to the most comprehensive log data available in order to better secure public and private companies, government, military and defense, and agencies tasked with providing and securing critical infrastructure worldwide.
Key Features & Capabilities:
- Advanced log data to support cyber incident reporting requirements, auditing, and compliance mandates
- Enhanced File Activity Monitoring (FAM) and Registry Activity Monitoring (RAM) capabilities to increase the speed-to-detection of anomalous activities
- The strongest security for network communications to-date
- Extended SQL event coverage captures more logs & log detail, providing an advanced level of log data to security teams using Microsoft SQL servers
- Enhanced Linux reporting capabilities and improved data granularity for Linux systems
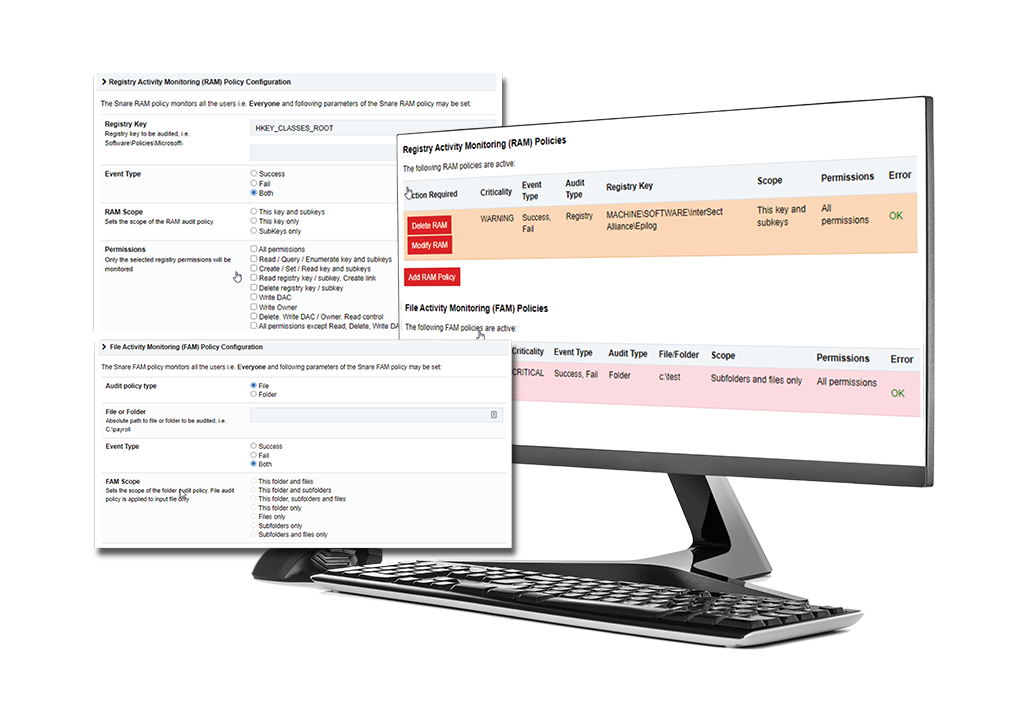
FAM & RAM Enhancements
IMPROVE THREAT DETECTION & RESPONSE TIME WITH INCREASED CONTROL OVER WHICH FILES ARE MONITORED
The latest version of Snare’s Enterprise Agents will provide IT stakeholders and security teams with the the most granular auditing and filtering capabilities for FAM and RAM logs ever released.
The new FAM and RAM auditing and filtering capabilities will provide security, risk, and compliance teams with options for File/Folder and Registry auditing. With v5.6, File/Folder and Registry access auditing can be controlled via the Snare Agent as well, with an option to apply additional event filters by user and text.
This means:
- More refined log data to meet auditing and compliance requirements
- Increased control over which files and registry locations are monitored
- The ability to concentrate on important events that are critical and filter out the noise
- Immediate access to the data required to report material cyber incidents
- The ability to reduce unwanted event log data
- Increased speed-to-detection in the event of a breach or attack
Sophisticated Security Capabilities
Strongest Security to Protect Data In Transit
With v5.6 of the Snare Agents, there is an option to use only TLS 1.3 to better protect the privacy and integrity of agent connections. The secure transmission of logs away from the system that created them – protecting data in transit.
This enhancement will enable security teams to:
- Enhance network security to use strongest ciphers and the latest TLS version
- Better secure network communications
- Reduce the risk for data tampering, and
- Quickly catch and prevent eavesdropping on communications
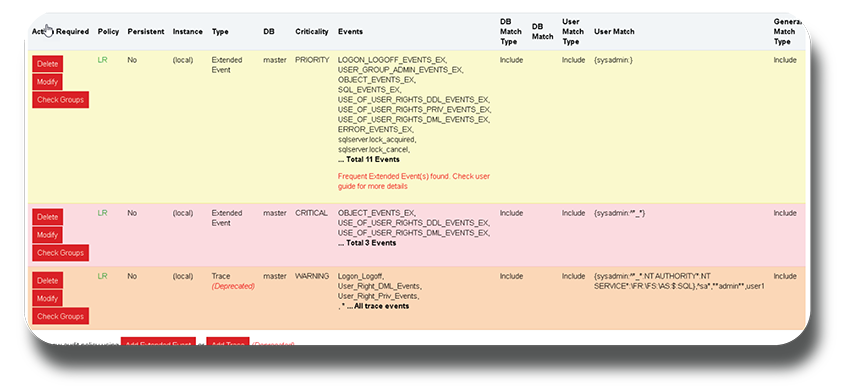
Extended SQL Event Coverage
Enhanced Database Auditing & Monitoring
The Snare Agent for Microsoft SQL Server can now be configured to collect Extended Events, enabling security teams to capture more events compared to SQL Trace.
The new View Extended Events page allows security teams to explore a tree of categories and events available on the current server, paired with a Filter to find events of interest by name. This makes threat detection and response faster and more comprehensive so security teams and IT stakeholders can confidently answer questions related to cyber incidents and breaches (who got in, how they got in, and what they stole).
Enhancements to the Snare Agent for SQL will enable security teams to:
- Access a more granular audit of database content and enhanced database performance metrics and statistics
- Collect as much or as little data required to identify anomalous actives in SQL Server
- Dramatically decreasing time spent on finding bad actors
- Use new event auditing options with extended coverage and very specific audit settings
- Collect enhanced audit events with additional detail and control
Additional OS Coverage
Ensure Audit Compliance Coverage Across More Operating Systems
With the latest version of the Snare Agents v5.6, additional OS coverage for Linux Agents using the SUSE Linux Enterprise Server 15 now supported.
This update to the Snare Agent will ensure coverage and audit compliance over corporate network assets and extend support for Snare agents on later operating systems.
Extended Linux Agent Coverage
Ensure All Relevant Audit Events Can Be Collected From Monitored Platforms
Updates and enhancement to the Snare Linux Agent will extend audit event coverage. The Snare Linux Agent can now be configured to collect any Linux audit event in the range of 1000 – 2599, previously it only covered from 1000-1199.
The enhancements to the Snare Linux Agent will help:
- Track more activity on the system and operating system behavior
- Extend the audit coverage for the Linux agent to collect other system and kernel events
- Ensure that all relevant audit events can be collected from the monitored platforms
Snare Central Capabilities
– Experience the Full Suite –
HIGH AVAILABILITY
High Availability helps to ensure there is minimal chance of lost log data, which is critical for forensic analysis in the event of a cyber attack or breach. High Availability also helps meet compliance regulatory requirements such as GDPR, ISO27001, and PCI DSS.
BACKUP & RESTORE
Helps to save on downtime and system rebuilds with simple Backup & Restore. Recover log data for forensic analysis or use the disk manager to view log data from backup locations.
600+ REPORTS | XDR & SYSMON
Over 600 reports cover new log types and threat hunting enhancements using Sysmon and additional log sources.
NEW LOG FORMATS
Enriched log data using newer Snarev2 and JSON formats allows for simpler data analysis with more granular log data formats. This includes Sysmon, Fortigate, Cisco, MacOs, Windows, and Snare v2 log formats.
COLOR CODING BY CRITICALITY
Report criticality is now visible on report icons. Users can set up reports based on criticality levels and what the they deem to be Low Priority (green) to High Priority (red). You can also filter your reports by criticality so you’re always focused on what’s most pressing.
DEDICATED TLS SYSLOG PORT
Snare Central includes a new dedicated TLS listener port for syslog collection.
OUT-OF-THE-BOX COMPLIANCE REPORTS
New compliance reports include CISA DNS, FIM, Agent Heartbeats, MacOS, and vCenter – all found in the Reports section of Snare Central.
RECEIVING SNMP v3 TRAPS
We now support receiving SNMP v3 trap data and it’s available to be analyzed within Snare Central 8.3 under the SNMPLog event type.
NETWORK STORAGE FOR BACKUPS
Redundancy is critical in cybersecurity compliance and Snare Central now supports Network Storage (CIFS or NFS) to back up your collected log data.
ENHANCED FILE INTEGRITY CHECK ADMINISTRATION
This tool allows the user to schedule, monitor, and administrate system files integrity checks and report on any changes on such files.
SNARE ENTERPRISE AGENTS
The industry’s best for Windows, Linux, Unix, macOS, Epilog, etc. – including FIM, RIM, FAM, RAM, and USB solutions.
Windows Agents Veracode Verified. No Java or .NET required
24x7x365 SUPPORTS
We have customers all over the globe and on every continent, so we are here to support you whenever you need it.
Ready for Snare Enterprise Agents?
Get in touch with your regional Snare office about upgrading or deploying Snare.