Enable. Extend. Enrich. IBM QRadar® XDR
In the event of a breach or hack, companies spend far too much time trying to sift through the noise to identify the threat, costing valuable time and money. Snare E3 for QRadar gets the right data to the right location at the right time for rapid response.
With Snare E3, you can:
- Enable your analyst to see what was stolen after a targeted intrusion
- Extend your visibility to see the actions of cyber attackers during dwell time of Human Operator Ransomware.
- Enrich your view of Privileged User Activity
Snare is Trusted by 4,000+ Enterprise Customers Worldwide
“Everything we have thrown at Snare has been handled flawlessly. E3 is pure genius in it’s approach, simplicity and enhancement of QRadar”
What is Snare E3?
Snare E3 Overview
Enable: Unlock the Potential of your SIEM by Adding Snare
Snare can give you all the core capability you need from SIEM at a fraction of the price and a fraction of the resources. With Snare E3 you can unlock your SIEM’s potential by enabling your team to:
- Manage the audit policy to only generate the events needed by your security policies
- Filter out redundant events
- Truncating verbose text of no forensic value
- Operate in real time vs batch
- Send to multiple destinations with different ports and protocols
- Manage EPS rates and bursts
- Over the wire encryption with TLS Auth
- Delve deeply into custom event logs
- Extract and forward Apps and flat file logs such as IIS
- Ensure integrity with dynamic DNS name and caching
- Scale up without needing a farm of servers to forward
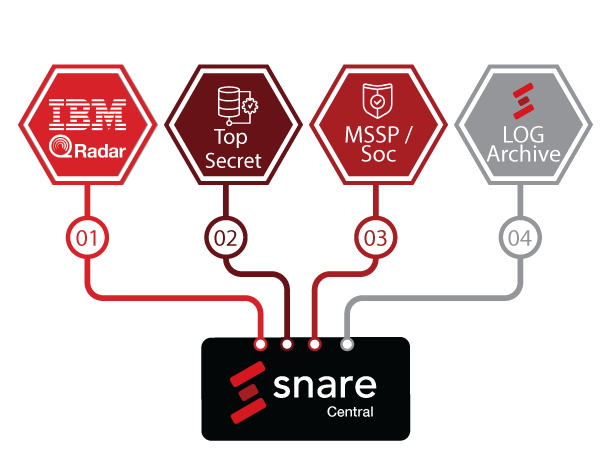
Extend Your Cybersecurity Profile without Provisioning More Servers
Extend your cybersecurity profile without provisioning or implementing more servers and more products from more vendors. Snare’s single lightweight agent extends from event logging to:
- Collecting relevant USB events
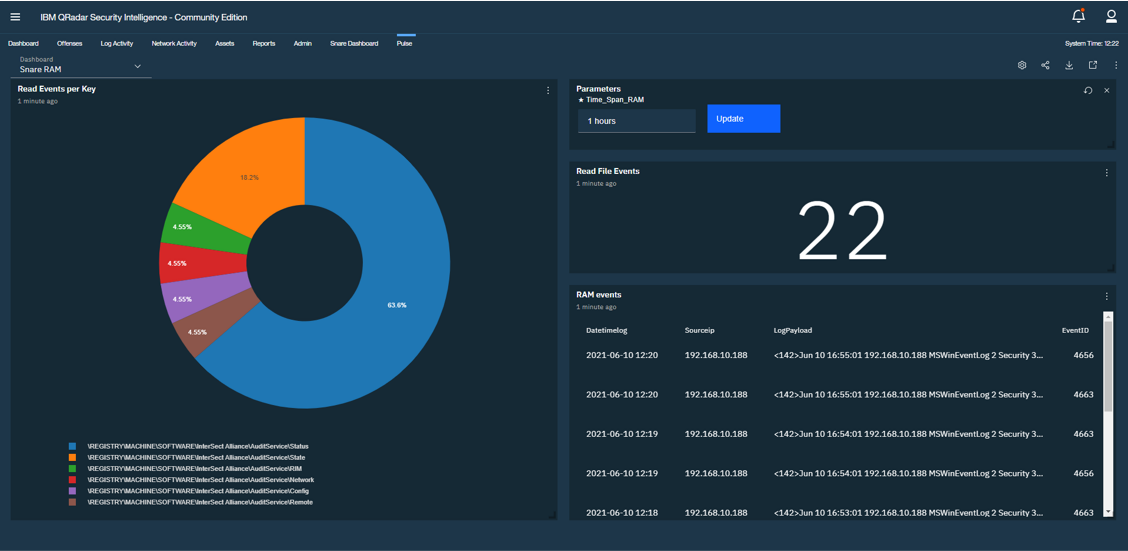
- Forwarding Registry Activity Events (RAM)
- Monitoring File Activity events (FAM) – knowing who accessed what files
- Checking on and reporting on the integrity of your file systems with a complete File Integrity Monitoring capability (FIM)
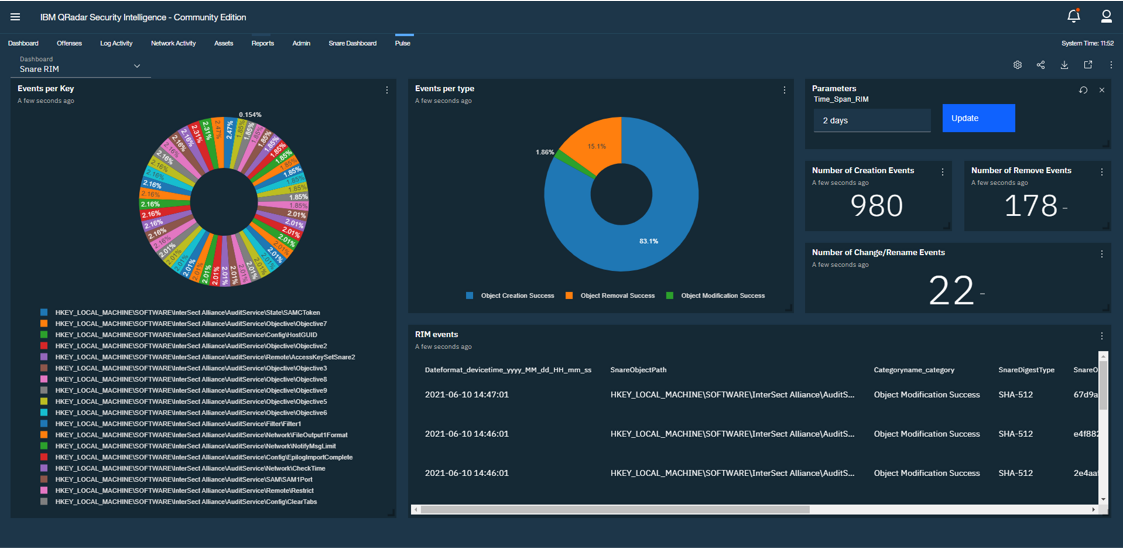
- Checking in and reporting on the integrity of your register (RIM), answering question like who just changed the output destination on the payroll reports
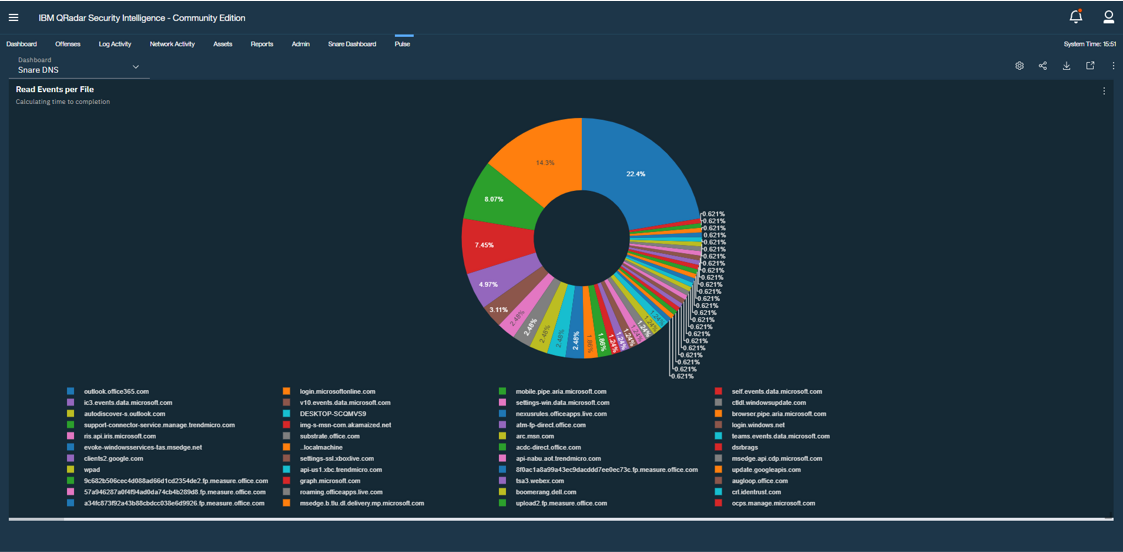
- Finding and forwarding Application Logs
- Monitor your privileged access to your SQL data (DAM)
- Across you surface including Desktops. servers, Mac, Linux, SQL. – cover all your surfaces
Enrich Your Cybersecurity Platform to Provide Unmatched Insights and Reduce MTTR
Enrich your cybersecurity platform to provide real-time unmatched insights and reduce your MTTR.
- Enrich your event logs with source identification data such as what department, division, program, agency, physical location, medical device is this event data associated to.
- Enrich your event data on its journey to identify which region, data center, geolocation the event data is coming from.
- Enrich your data by masking things such as PII, so as to be able to send on to external 3rd parties while maintaining privacy compliance.
- Enrich your data with Snare plus Sysmon, bringing forward critical event data such as SHA1, command line and parent processes, process GUI and more.
“I tend to use Snare when customers have a lot of end points, 1,000 or more though particularly over 10K windows end points and they know they want to monitor each and every one of them. I know Snare will report in every time, all the time, even in large scale environments. Snare is well documented and easy to install. Snare also does encryption from the agent to the QRadar host, which is very important for most organizations, though in particular federal customers.”
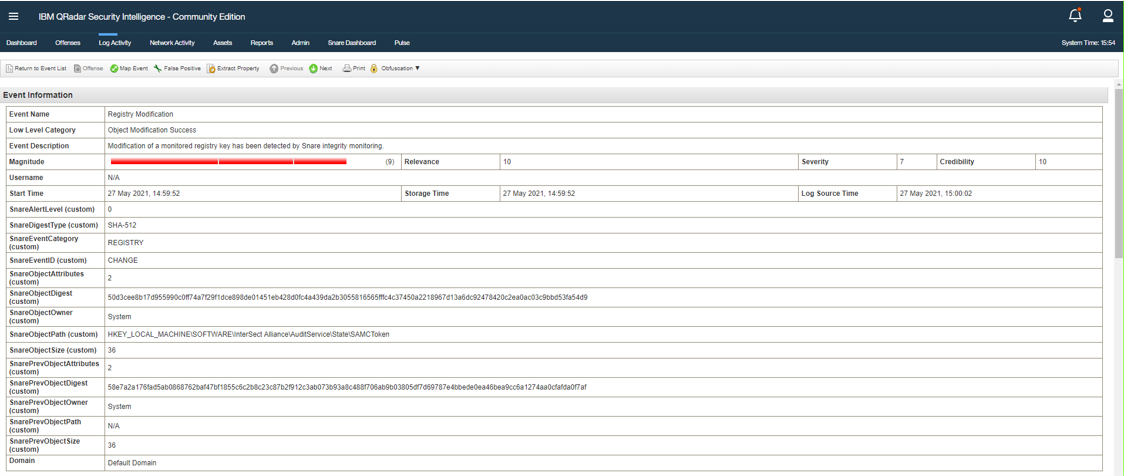
Custom DSM
A QRadar Device Support Module is a parser. There is a new and enhanced DSM for Snare. Please ensure you obtain that and apply it to your QRadar instance. The image shows some of the new fields available from the new DSM, such as integrity hashes on registry objects to identify when things change.
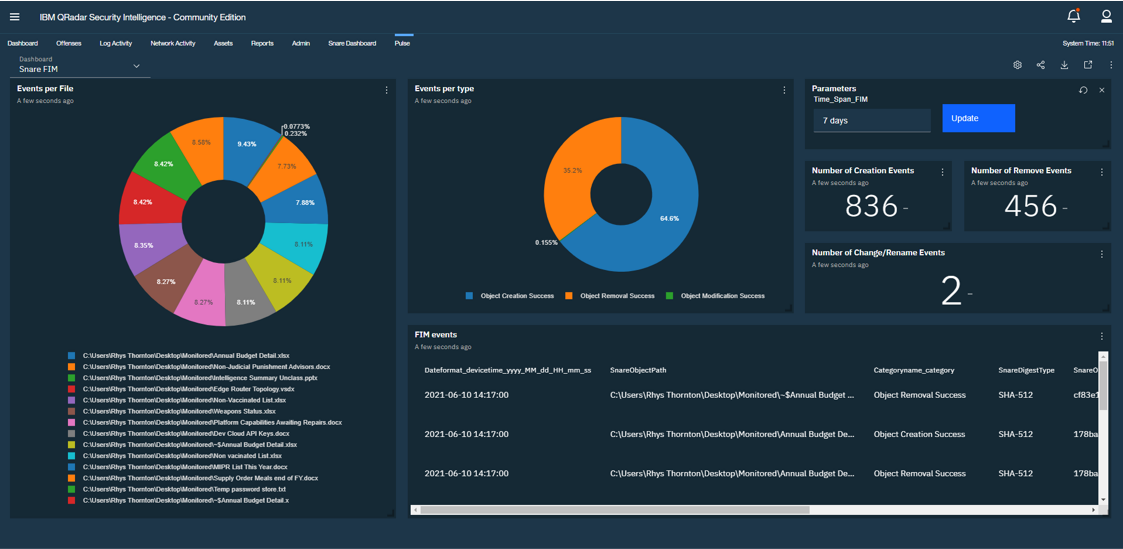
File Integrity Monitoring (FIM)
Many regulations require the addition of a checksum to detect file changes and file permission changes, such as PCI DSS that require the change detection tools be run at least weekly. Snare runs an integrity hash on critical data files. When the intruder accesses that file, the integrity hash changes, and Snare alerts you to that change.
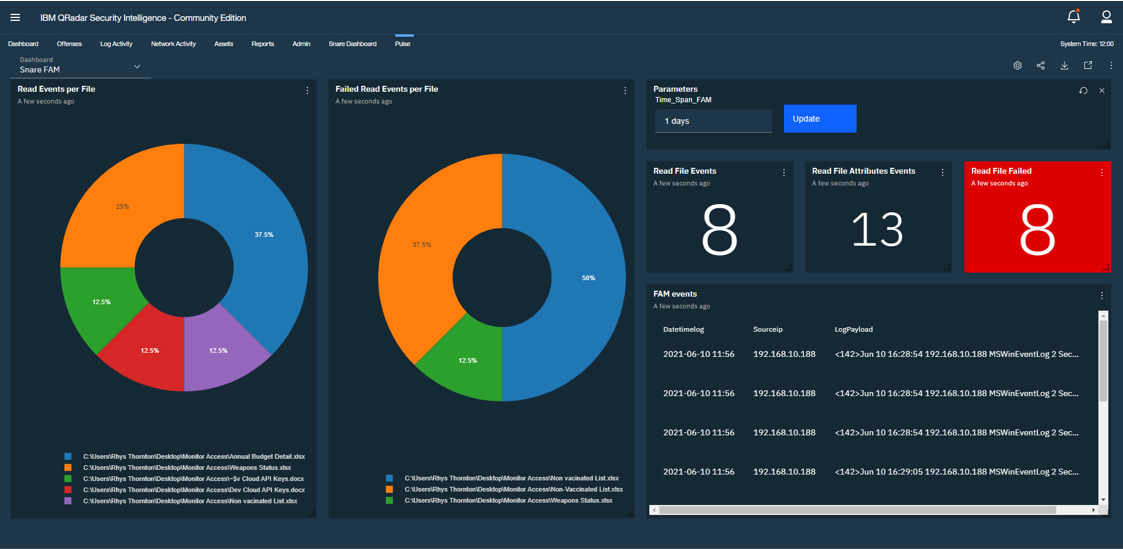
File Activity Monitoring (FAM)
File Activity Monitoring reveals who tried and/or failed to access files. This step alone is very important when your MS Windows network shares are locked down very well. It is important to monitor who is even trying to access critical data, so that appropriate steps can be taken.
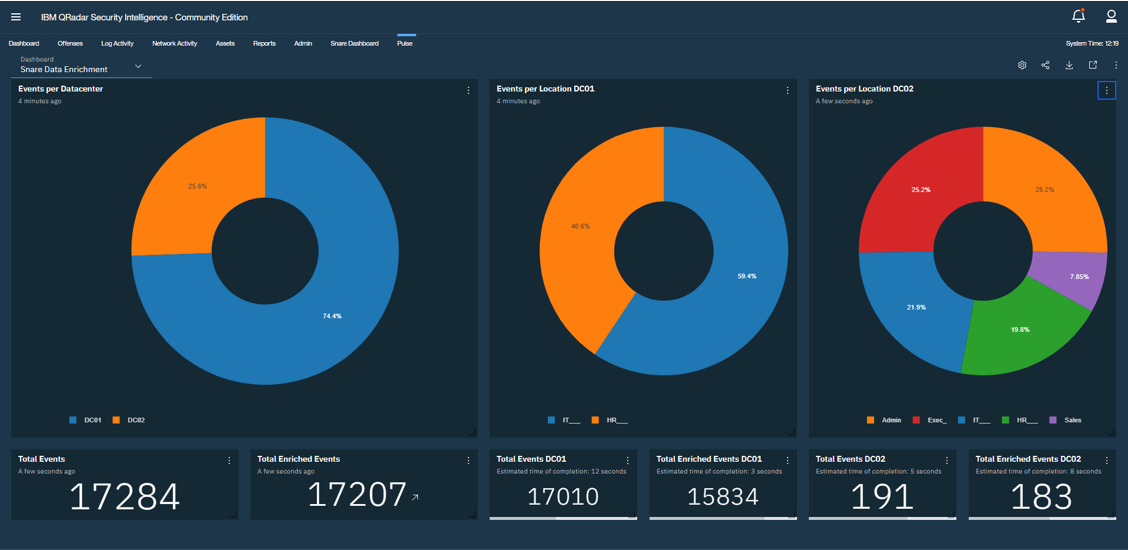
Data Enrichment
With Snare, you can enrich your data with any label you wish. For example, you can quickly identify where an asset is located geographically, or by business unit. In Snare, the EventSource ID field can add any string into an event. For example, all business unit logs can be tagged with their business unit. Use REGEX in Snare to write the “tag” to the event. The right anchor is an underscore in this case. Use QRadar to extract the custom field tag. Now the Snare/QRadar user can sort all data by business unit.
Featured Content
Using Snare to Detect Solarigate Backdoor Delivered by SolarWinds Orion Software
This blog contains some immediate guidance on using Snare agents and Snare Central to detect activity on your network from the Sunburst Backdoor malware delivered by SolarWinds Orion Software.
Ready to talk about Snare E3’s Suite for QRadar XDR?
Get in touch with our team