In 2017 defense contractors became subject to a cybersecurity mandate by the Federal Government, starting with the Defense Acquisition Federal Regulation Supplement. DFARS required DoD Contractors to adopt cybersecurity standards according to the NIST SP 800-171 Cybersecurity Framework.
On January 30, 2020, the Department of Defense released version 1.0 of the Cybersecurity Maturity Model Certification (CMMC) to ensure cybersecurity controls and processes would be put in place to protect controlled unclassified information (CUI) on DoD contractor systems.
CMMC will be mandatory for 300K Government Contractors, establishing cybersecurity as a foundation for future DoD Acquisitions. This imposes cybersecurity requirements on a large base of contractors that has never dealt with Federal Contractor Information (FCI) requirements.
CMMC requirements will flow down to all subcontractors from prime contractors. All future RFPs will require adherence to various levels of CMMC. Government Contractors will have to pass a CMMC audit so they can become certified and continue to offer their products and services to the DoD. The required CMMC level will be a pass/fail evaluation at the proposal stage for contract awards. Contracts will not be awarded to organizations that do not meet the required level.
Between June and September of 2020, the initial round of audits will begin for a select number of Department of Defense Programs/RFIs, with the required CMMC Levels identified. A CMMC 3rd Party Assessment Organization (C3PAO) will ask Defense Contractors to prove how they process, store and transmit Controlled Unclassified Information (CUI). Government Contractors will need to be certified to the required Level in order to receive and bid on the RFP.
The timing of Accreditation Audits is now projected to be Q4 2020 (Calendar) going forward, with RFI’s including CMMC references as early as June and RFPs including CMMC references by Q4.
CMMC requires policy, process and plan documentation covering all security domains
The CMMC Model has 5 Levels with a number of defined Practices and Processes in each Level
| NIST Controls | |||
| Level 1 | 17 | Basic Cyber Hygiene | Basic safeguarding of FCI |
| Level 2 | 65 | Intermediate Cyber Hygiene | Transition step to protect CUI |
| Level 3 | 119 | Good Cyber Hygiene | Protecting CUI |
| Level 4 | 123 | Proactive | Protecting CUI and reducing risk of APTs |
| Level 5 | 128 | Advanced/Progressive | Protecting CUI and reducing risk of APTs |
Government Contractors can use the “Self Assessment Handbook – NIST Handbook 162” provided by the National Institute of Standards and Technology (NIST).
CMMC Level 3 is based on compliance with NIST 800-171, plus 20 additional Practices, including the following:
Access Control:
- Limiting information system access to authorized users
- Separating the duties of individuals to reduce the risk of malevolent activity
- Prevent non-privileged users from executing privileged functions and capture the execution of such functions in audit logs
- Prevent unauthorized access using authentication and encryption
Audit and Accountability
- Create and retain system audit logs and records to enable monitoring, analysis, investigation and reporting of unauthorized system activity
- Review and update logged events
- Alert in the event of an audit logging process failure
- Collect audit information (logs) into one or more central repositories
- Protect audit information and audit logging tools from unauthorized access, modification and deletion
- Correlate audit record review, analysis and reporting processes for investigation and response to indications of unlawful, unauthorized, suspicious or unusual activity
- Provide audit record reduction and report generation to support on-demand analysis and reporting
Media Protection
- Implement cryptographic mechanisms to protect the confidentiality of CUI stored on digital media during transport
- Save security event log data in one or more central repositories
Recovery
- Regularly perform complete, comprehensive and resilient data backups
Security Assessment
- Monitor security controls on an ongoing basis to ensure the continued effectiveness of the controls
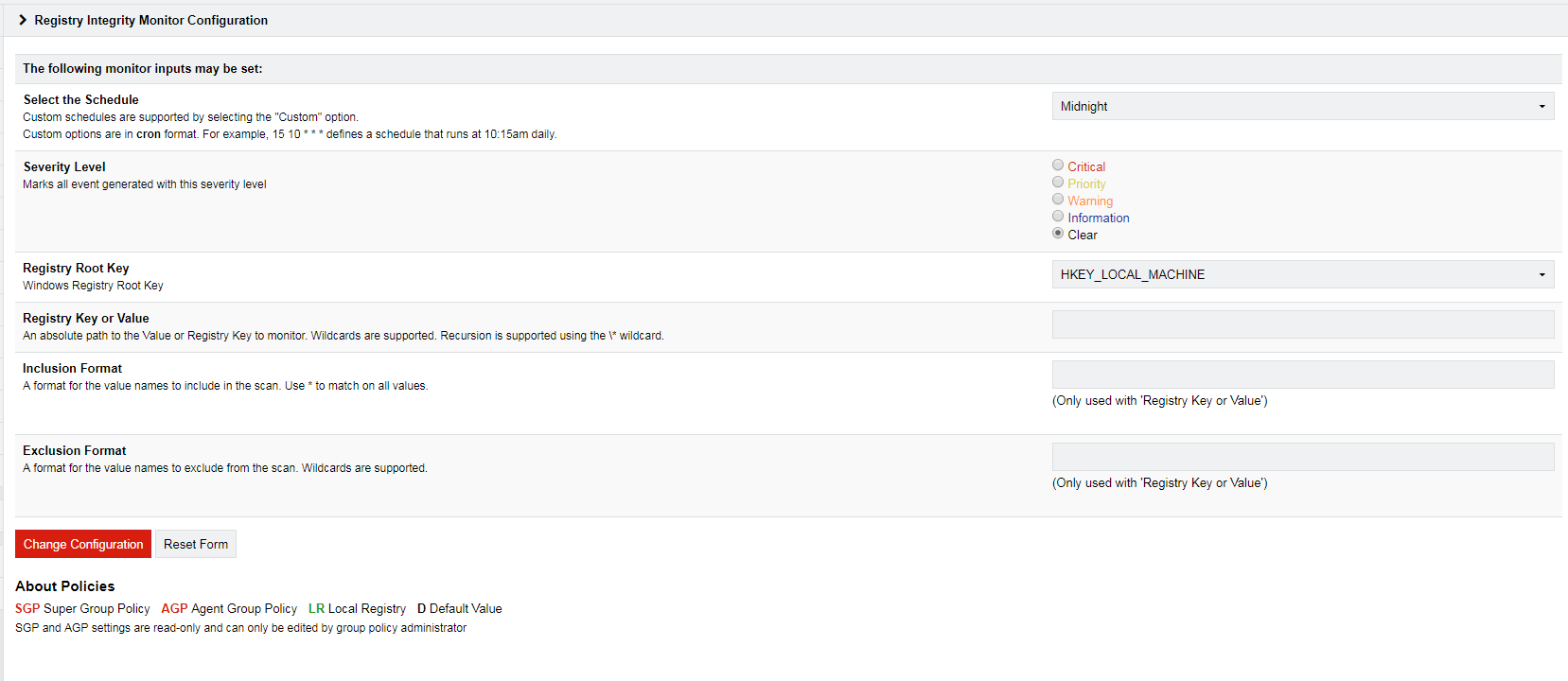
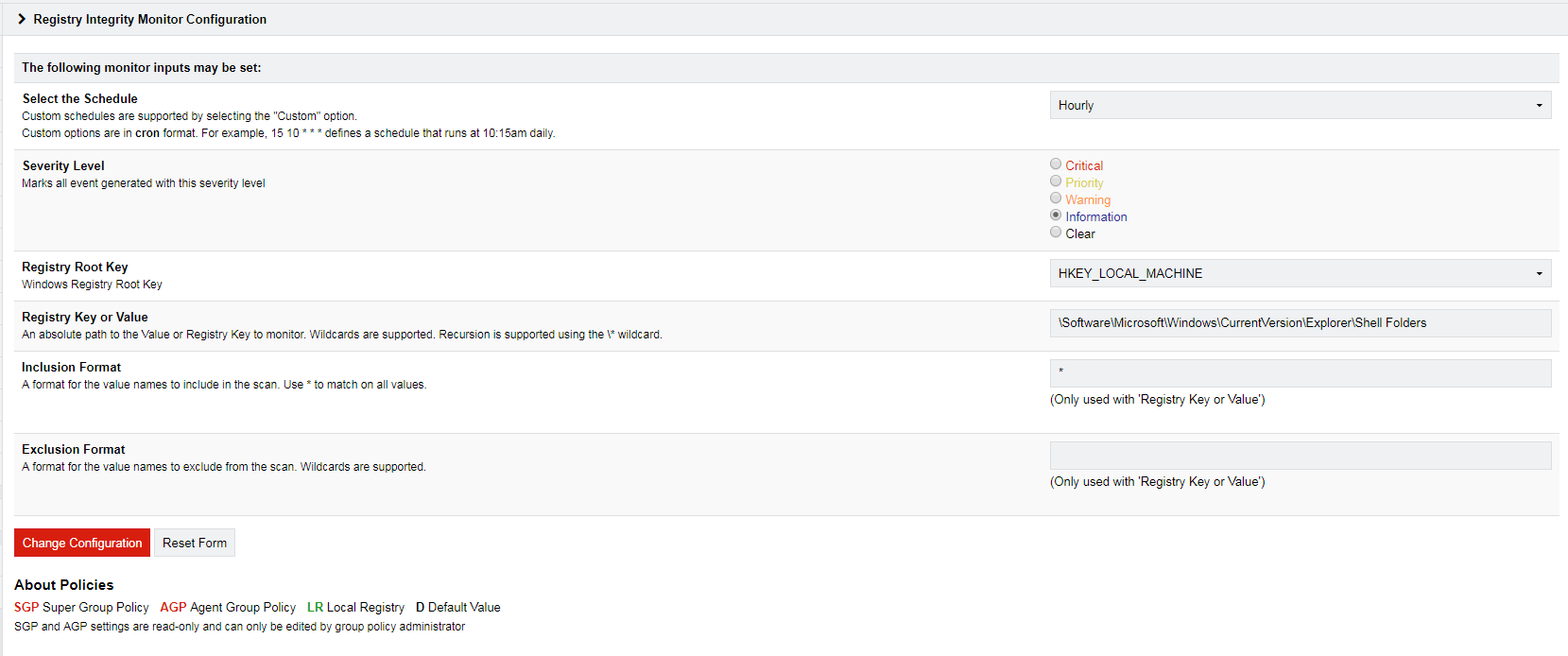
Level 3 of the CMMC model specifically points to the requirement for Security Event Log Management Software.
Prophecy International has been providing Event Log Management Solutions to the Intelligence Community, Military, Non-Military and Government Contractors for over 15 years, and continues to invest in software that supports event log collection, forwarding, analysis and reporting. SNARE Enterprise Agents and Log Management Servers will help government contractors address CMMC Level 3 Requirements.
More information about SNARE Log Management Software can be found at www.snaresolutions.com, with options for a software demonstration and free supported software trials.